The Risks and Vulnerabilities of Unsecured CDP and LLDP Protocols
The information exchanged between neighbors may be obtained by these two protocols, which send data to a multicast destination MAC address (CDP: 01-00-0c-cc-cc-cc and LLDP: 01:80:c2:00:00:0e).
As long as we know the source and destination MAC addresses of the traffic, we may utilize L2 ACL to block it or deactivate it for any interface that is linked to an untrusted device.
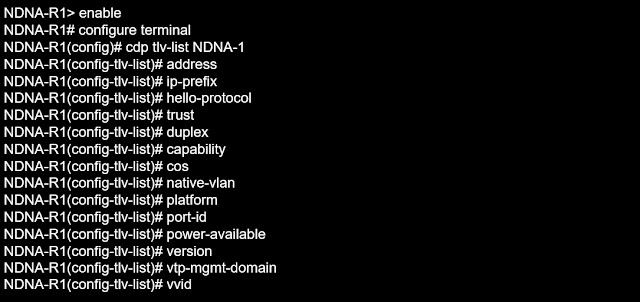
There is another way to customize these protocols rather than disabling them because they send some predefined fields (Type, Length, Value) that we can be selected, so we can choose the list or profiling.
⭐Related : Network Discovery Protocols : CDP and LLDP
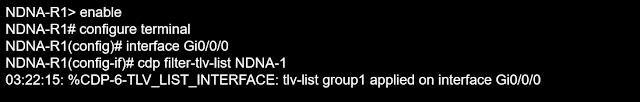
To create the customized L2 DP, we may specify the TLV list and use it globally or per interface. As an example, let's utilize Cisco.
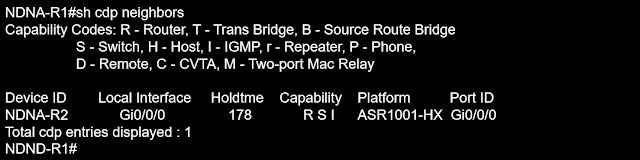
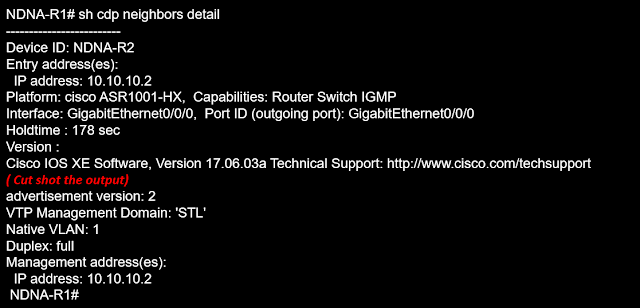
We have two devices connected, let us show the normal CDP exchange information that occurs between neighbors
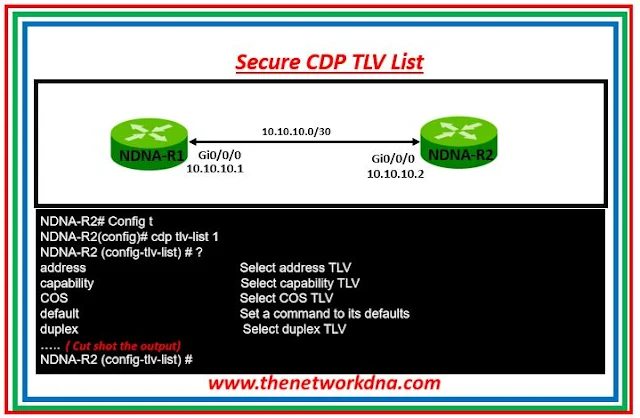 |
| Fig 1.1- Secure cdp tlv list |
If the client refuses to provide a network map or design, we will search for L2 DP assistance. Additionally, control plan CDP will assist us in identifying misconfigurations. These are just a few examples of how L2 discovery protocol assists us in our day-to-day operations.
Continue Reading...
- DNAC Device PNP Onboarding Process for IOS-XE
- Cisco DNA center Fabric QOS overview
- How to run a template from Cisco DNA Center
- Updates in Cisco DNA Center 2.3.7.0
- Updates in Cisco DNA Center 2.3.5.0
- Installing Cisco DNA Center appliance: Knows about Ports
- Updates in Cisco DNA Center 2.3.4.x
- Virtual Appliance Cisco DNA Center on Amazon AWS
- Cisco DNA Center Guardian Version 2.3.3.x - Host entry cleanup in Maglev